![]() We are no longer updating this content regularly. Please visit our knowledge base for most current version.
We are no longer updating this content regularly. Please visit our knowledge base for most current version.
Overview
The feature helps the administrator to maintain the computer object in a group based upon the chassis. The computer object can be added to a specified security group ex. "Domain Laptops" depending on the chassis type of the computer
Purpose
This article provides instructions on testing the SYNERGIX AD Client Extensions software Account Attributes \ Computer Account Attributes \ Computer Object Group feature. The software requires the security principal Domain Computers or the security group 'SYNERGIX ADCE Managed Computers' is granted permission to 'READ MEMBER' and 'WRITE MEMBER' on the "chassis based" security groups
Prerequisites
- Supported Microsoft Windows Operating System
- Microsoft Windows XP or
- Microsoft Windows Vista or
- Microsoft Windows 7.0 or
- Microsoft Windows 8.0
- .NET Framework 4.0
- Active Domain Membership in Microsoft Active Directory domain
- Microsoft Outlook or other EMail client
- EMail client is required to submit log files to support@synergix.com or x@mail.asana.com
- SYNERGIX AD Client Extensions 2013
Active Directory Domain Environment
- Single Active Directory Domain environment i.e. Single Forest with Forest Root Domain only example. F10.LOCAL
- You can setup a more complex Active Directory Domain environment, if needed. For example, one forest F10.LOCAL with child domains D10.F10.LOCAL, D11.F10.LOCAL and D12.F10.LOCAL and a trusted forest F20.LOCAL with child domains D20.F20.LOCAL, D21.F20.LOCAL and D22.F20.LOCAL
- Security Group(s)
- Create a security group called "SYNERGIX ADCE Managed Computers". The group type may be Domain Global Group or Domain Local Group ,similarly create security groups for Domain Desktop, Domain laptops, Domain other computers.
- Add the test domain computer(s) into the security group "SYNERGIX ADCE Managed Computers"
- Delegate Control
You must ensure that security principal Domain Computers or the security group 'SYNERGIX ADCE Managed Computers' is granted permission to 'READ MEMBER' and 'WRITE MEMBER' on the "chassis based" security groups(Domain laptops, Domain desktops, Domain other computers) .
- Configure domain Group Policy Object
- Copy SYNERGIX AD Client Extensions Administrative Template file SYNERGIX-ADCE.ADMX to %SystemRoot%\PolicyDefinitions on admin workstation ( must be Windows 7.0 )
- Copy SYNERGIX AD Client Extensions Administrative Template Language file SYNERGIX-ADCE.ADML to %SystemRoot%\PolicyDefinitions\en-US on same admin workstation ( must be Windows 7.0 )
- Using GPMC.MSC, edit existing or new Group Policy Object.
- In Group Policy Editor, expand COMPUTER CONFIGURATION
- Expand Administrative Templates
- Expand SYNERGIX AD Client Extensions
- Expand Account Attributes
- Expand Computer Account Attributes
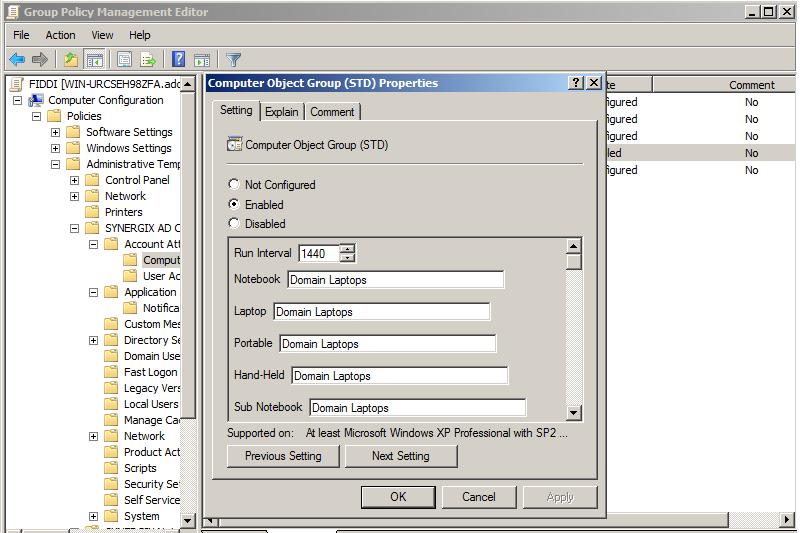
- Select Computer Object Group
- Enable policy setting
- The run interval value determines the time interval before next update occurs. By default, it is 1440 minutes.
- Enter the group names in the box for example if you want the Domain laptops to be added into the security group Domain laptop then specify Domain laptops in the laptop box
More Information
- Visit Synergix website or contact vendor support
Procedure
- Log into a domain computer with local administrative privileges
- Install SYNERGIX AD Client Extensions software
- Ensure the SYNERGIX AD Client Extensions specific Group Policy settings were applied
- Launch RSOP.MSC or run GPRESULT.EXE /v to confirm
- Logout
- Log into the same domain computer with a domain user account. This domain account represents a business user who does not have elevated privileges on his / her computer.
- Launch Active Directory Users and Computers ( dsa.msc ) Management Console
- If DSA.MSC is not installed, log into another workstation with Administrative Tools installed and then, launch DSA.MSC on it
- Search The security group Domain laptops
- The Test laptop computer will be added to the group Domain laptops
- If Yes, Test Results are successful. In the Test Result, write down PASS
- If No, re-run test
- Remove lastUpdate registry entry from HKEY_LOCAL_MACHINE\SOFTWARE\Synergix\ADCE\Account Attributes\Computer Account Attributes\Computer Object group. Did it work this time ?
- Try on another computer. Did it work this time?
- Review ServiceLogFile.txt. Do you see "Access Denied" exception? If yes, verify that the security principal Domain Computers or the security group 'SYNERGIX ADCE Managed Computers' is granted permission to 'READ MEMBER' and 'WRITE MEMBER' on the "chassis based" security groups
Test Results
- Pass or
- Fail
Test Result Submission
- Complete the Test Environment worksheet
- Upload test results document file to software test repository
- Upload log files
- ServiceLogfile.txt
- ClientLogfile.txt
- Output of GPRESULTS.EXE /V command
Note: You must use ADCE \ Help \ Submit Log Files button to zip up above 3 files and submit
References
N/A
0 Comments