![]() We are no longer updating this content regularly. Please visit our knowledge base for most current version.
We are no longer updating this content regularly. Please visit our knowledge base for most current version.
Overview
This feature enables IT Security Officers and IT Managers to read the audit logs that display Local Administrator Password Retrieval attempts.
The Audit Password Retrieval feature can be configured using the Administrative Template file that is provided with the software.
The feature assumes following organizational roles have been defined
- IT Support Professional / Windows Systems Administrators who need to retrieve the password of Local Administrator Account.
- Audit Readers who need to review the audit logs and generate reports.
- Audit Administrators who need to perform necessary housekeeping of the audit logs and remove stale records.
Active Directory Security Groups are used to manage the above mentioned roles
- SYNERGIX ADCE Managed Computers
This group contains computer objects and user objects. All domain computers that have the software installed are made member of this group. IT Support Professional and Windows Systems Administrators who are allowed to read the password are also member of this group.
*This security group is also used for product licensing purposes and for defining the security filtering in the GPO that is configured.
- SYNERGIX ADCE Managed Audit Readers
This group contains user objects. Members of this group fulfill the Audit Readers role. They can read the audit entries and generate a report file.
- SYNERGIX ADCE Managed Audit Administrators
This group contains user objects. Members of this group fulfill the Audit Administrators role. They may perform housekeeping work. They cay permanently delete audit entries that have become stale. They can also use standard Active Directory tools to export the entries in raw format.
- Domain Admins or delegated Administrators
Each Audit Log entry is stored in a Device object in Active Directory. The default container for Audit Log entries is CN=ADCE,CN=SYNERGIX,CN=Program Data in the default naming context.
The Domain Administrators may delegate the right to SYNERGIX ADCE Managed Audit Administrators security group or initialize the required container on their own.
Purpose
The Built-In Administrator Account Password Management feature sets complex and unique password on Windows computers. Designated systems administrators may use the software to retrieve Local Administrator Password on specific domain computer.
The Local Administrator Password Retrieval attempts can be audited when the Auditing Local Administrator Password Retrieval feature is enabled.
This article provides instructions on testing the SYNERGIX AD Client Extensions software. The Local Administrator Password Retrieval attempts feature is configured using the Administrative Template. After installing the Administrative Template file, the policy setting can be found under COMPUTER CONFIGURATION \ Administrative Templates \ SYNERGIX AD Client Extensions \ Application Settings \ Audit Policy \ Local Account Password Audit Policy. The Explain tab of the Group Policy setting provides online instructions on configuring the feature.
Prerequisites
- SYNERGIX AD Client Extensions 2015 or higher
- Supported Microsoft Windows Operating System
- Microsoft Windows XP SP3 or
- Microsoft Windows 7.0 SP1 or
- Microsoft Windows 8.x
- Microsoft Windows 10.0
- .NET Framework
- .NET Framework 4.0 for SYNERGIX AD Client Extensions 2015
- Domain Membership in Microsoft Active Directory domain
- Microsoft Outlook or other EMail client for Microsoft(R) Windows(TM)
- EMail client is required to submit log files to support@synergix.com or x@mail.asana.com
Active Directory Domain Environment
- Single Active Directory Domain environment i.e. Single Forest with Forest Root Domain only example. F10.LOCAL
- You can setup a more complex Active Directory Domain environment, if needed. For example, one forest F10.LOCAL with child domains D10.F10.LOCAL, D11.F10.LOCAL and D12.F10.LOCAL and a trusted forest F20.LOCAL with child domains D20.F20.LOCAL, D21.F20.LOCAL and D22.F20.LOCAL
- Security Group(s)
- Create a security group called "SYNERGIX ADCE Managed Computers". The group type may be Domain Global Group or Domain Local Group.
- Add the test domain computer accounts into the security group "SYNERGIX ADCE Managed Computers"
- Add systems administrators domain accounts into the security group "SYNERGIX ADCE Managed Computers"
- Delegate Control
- Not applicable for configuring this feature when default attribute value otherMobile is used.
- In recommended configuration, you can select an attribute that can be marked as confidential attribute and then, delegate control to write to it. The security group "SYNERGIX ADCE Managed Computers" must be allowed to write to houseIdentifier attribute value.
- Configure domain Group Policy Object
- Copy SYNERGIX AD Client Extensions Administrative Template file SYNERGIX-ADCE.ADMX to %SystemRoot%\PolicyDefinitions on admin workstation (must be Windows 7.0 or higher)
- Copy SYNERGIX AD Client Extensions Administrative Template Language file SYNERGIX-ADCE.ADML to %SystemRoot%\PolicyDefinitions\en-US on same admin workstation (must be Windows 7.0 or higher)
- Using GPMC.MSC, edit existing or new Group Policy Object.
- In Group Policy Editor, expand COMPUTER CONFIGURATION
- Expand Administrative Templates
- Expand SYNERGIX AD Client Extensions
- Expand Application Settings
- Expand Audit Policy
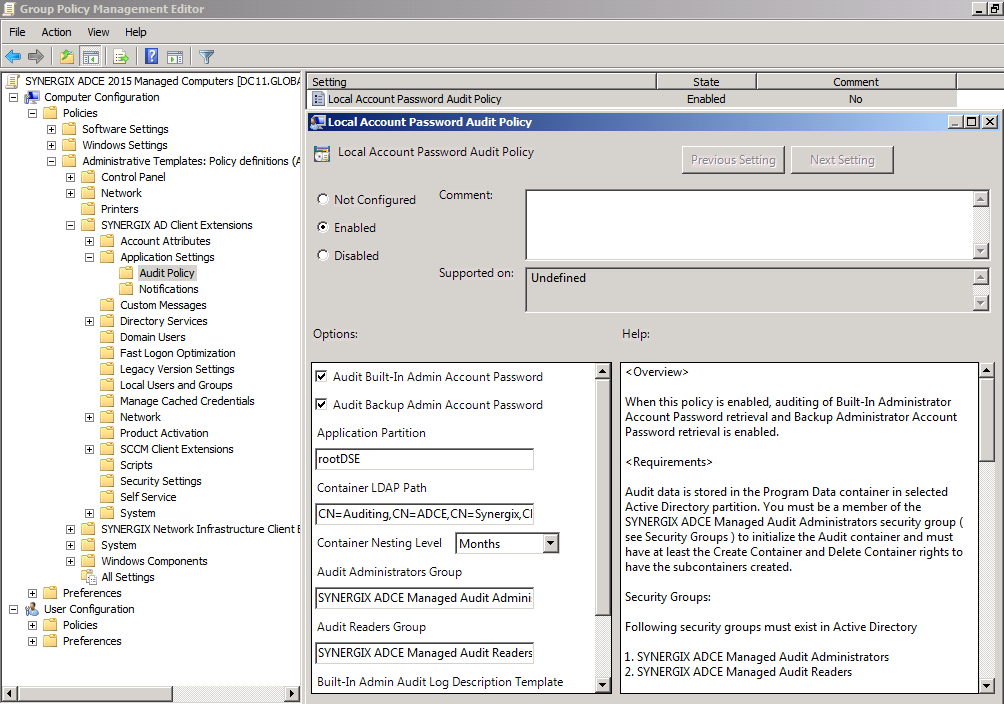
- Select Local Account Password Audit Policy setting
- Click on the Enable radio button to enable the policy setting
- Check Audit Built-In Admin Account Password
- Check Audit Backup Admin Account Password
- For Application Partition, leave the value as rootDSE. This value will use the default naming context as the partition to store the audit entries.
- In the Container LDAP Path specify the relative distinguishedName. Default value CN=Auditing,CN=ADCE,CN=SYNERGIX,CN=Program Data.
- Note: You can use ADSIEDIT.MSC to create the container object Auditing in the specified path under CN=Program Data
- In the Container Nesting Level, specify how the audit entries will be categorized, by day, by month or by year. Default value is Months.
- For the Audit Administrators Group, specify a security group you have created. By default, it is SYNERGIX ADCE Managed Audit Administrators security group. Add user accounts in this security group who will be responsible for the housekeeping of the audit entries.
- For the Audit Readers Group, specify a security group you have created. By default, it is SYNERGIX ADCE Managed Audit Readers security group. Add user accounts in this security group who will be responsible for the viewing the audit entries and generating reports.
- The role to retrieve the Local Administrator Password is managed by the group configured under SYNERGIX AD Client Extensions \ Application Settings \ Admin Tools Settings policy. Add user accounts in this security group to allow designated administrator to read Local Administrator Account Password
- You may leave the Description Template with default value
- You should leave the Search Filter with default value.
- Click OK to save the Group Policy settings.
More Information
- Visit Synergix website or contact vendor support
Procedure
1. Initialize Audit Logs container
- Ensure that the Domain Admin has created sub-container CN=ADCE,CN=SYNERGIX,CN=Program Data and granted permissions to initialize the container. Alternatively, you can use a Domain Admin account to initialize the required container object.
- Ensure your (admin) account is member of the SYNERGIX ADCE Managed Audit Administrators security group.
Note: Even if you are using a Domain Admin account to complete this task, it should still be a member of the SYNERGIX ADCE Managed Audit Administrators
- Log into a domain computer with the domain account ( your admin account ) that has local administrative privileges on the workstation.
- Ensure the SYNERGIX AD Client Extensions specific Group Policy settings were applied
- Launch RSOP.MSC or run GPRESULT.EXE /v to confirm
- Install SYNERGIX AD Client Extensions software
- After the software is successfully installed, double click on the orange icon in the system tray.
- You should see Admin Tools ( click here ) in the menu bar. It is visible only to members of the SYNERGIX ADCE Managed Audit Administrators security group.
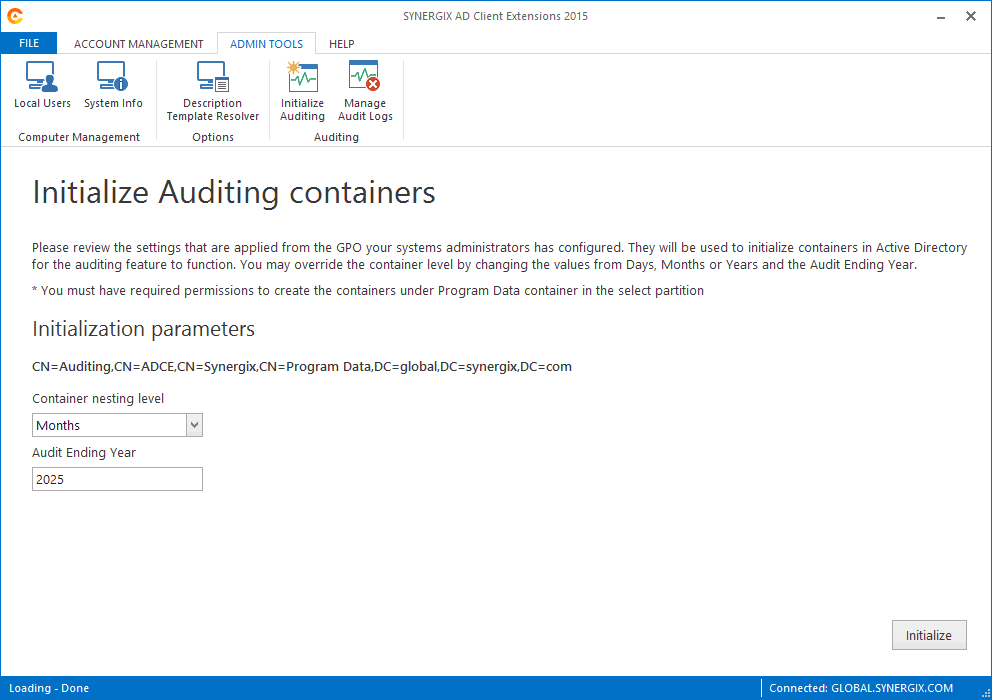
- Click on Initialize Auditing button
- Select the container nesting level and audit ending year. You may leave default values.
- Click on Initialize button.
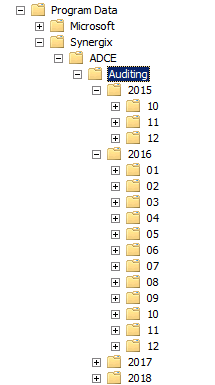
- Launch Active Directory Users and Computer ( DSA.MSC ) and verify that the container CN=Auditing,CN=ADCE,CN=SYNERGIX,CN=Program Data has new sub containers reflecting the months and the years.
2. Retrieving Local Administrator Account Password
- Ensure your (admin) account is member of the SYNERGIX ADCE Managed Computers security group
- Log into a domain computer with the domain account ( your admin account ) that has local administrative privileges on the workstation.
- Ensure the SYNERGIX AD Client Extensions specific Group Policy settings were applied
- Launch RSOP.MSC or run GPRESULT.EXE /v to confirm
- Install SYNERGIX AD Client Extensions software
- After the software is successfully installed, double click on the orange icon in the system tray.
- You should see Admin Tools ( click here ) in the menu bar. It is visible only to members of the SYNERGIX ADCE Managed Computers security group.
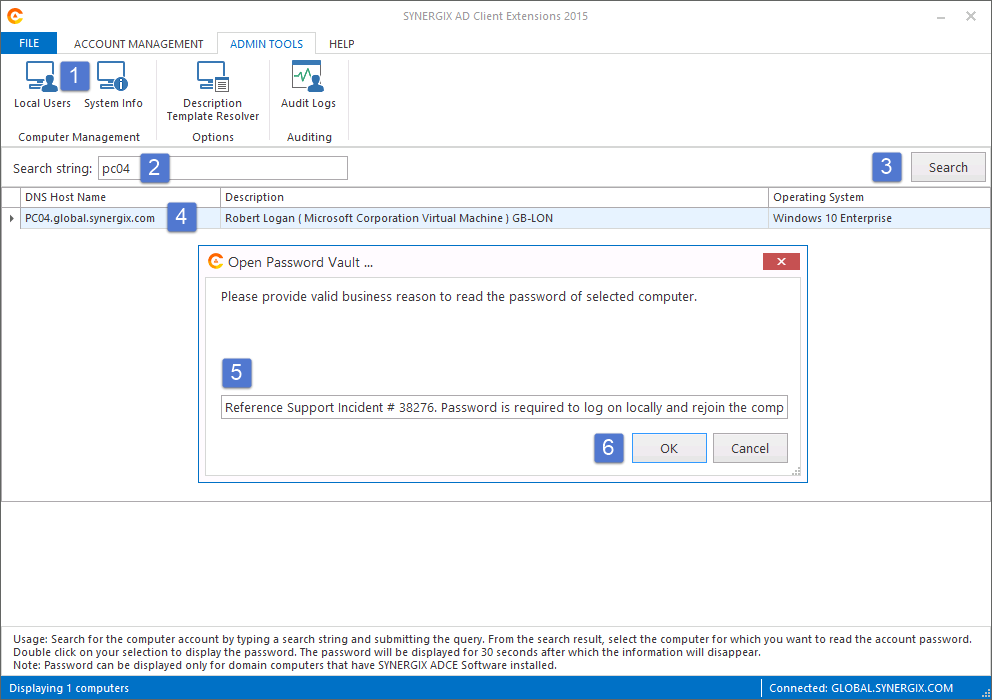
- In the Search String enter the first three characters of domain computers which you want to retrieve the password.
- Select a computer from the list. Double click on it.
- You will be prompted to enter a reason to retrieve the password.
- You should be able to see the decrypted password string for the Built-In Administrator Account and for the Backup Administrator Account, when configured.
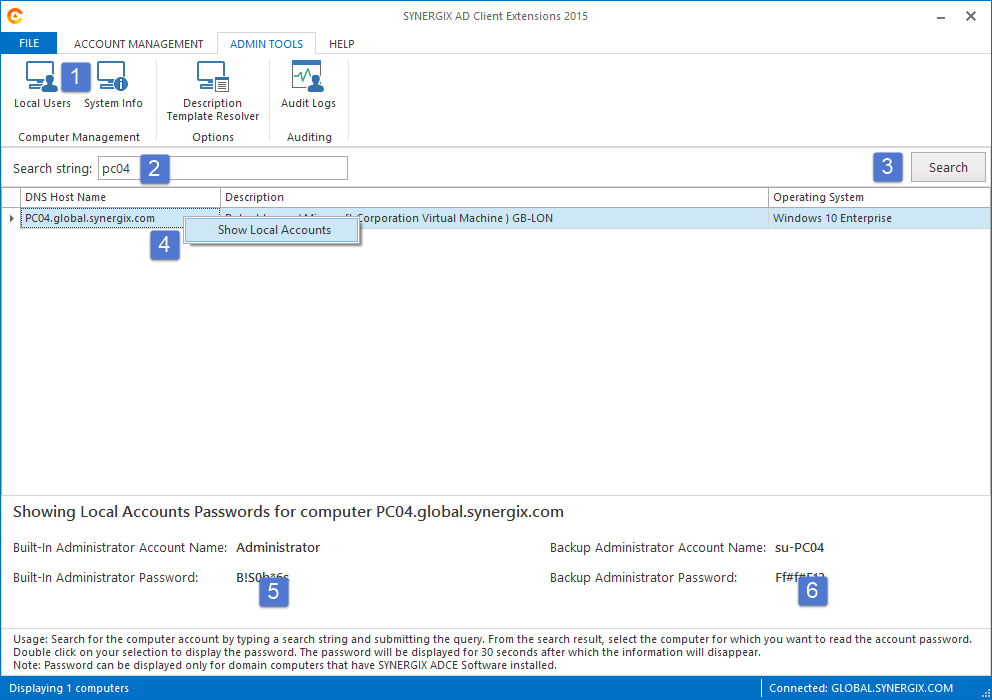
- You can configure Backup Administrator Account Password GPO setting to create a new local account and manage its password too. By default, the backup administrator account is created using the su-%computername% template.
- Note the acronym su simply means super user. You can create a template of your choice.
- Ensure your (admin) account is member of the SYNERGIX ADCE Managed Audit Readers security group.
- Log into a domain computer that has SYNERGIX AD Client Extensions software installed already.
- Double click on the Synergix orange icon in the system tray.
- You should see Admin Tools ( click here ) in the menu bar.
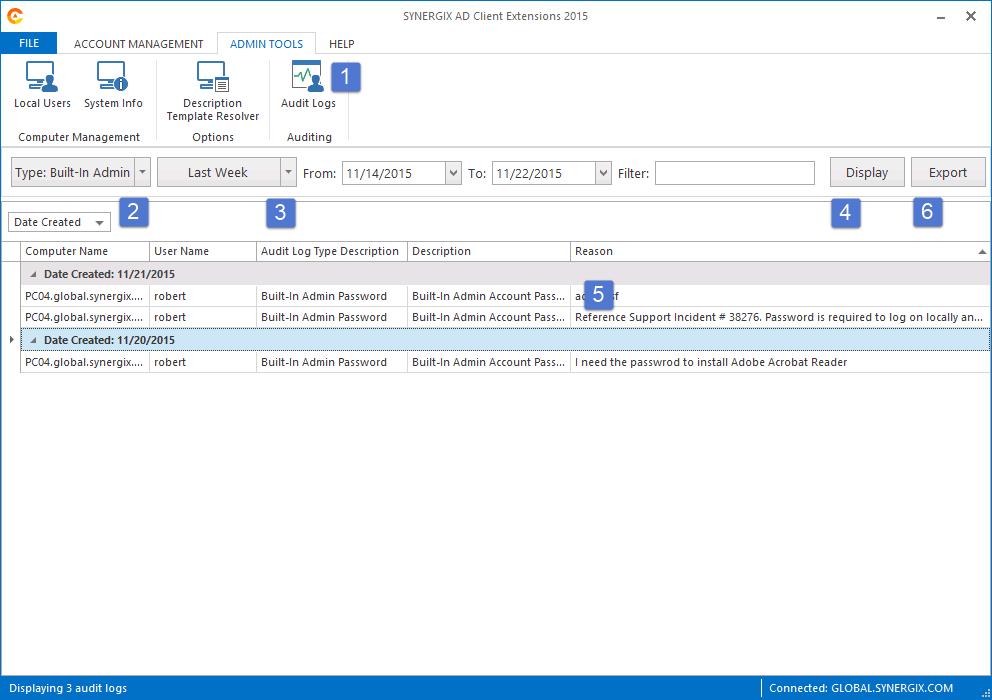
- Click on Audit Logs button
- Select the type and time range window as appropriate and click on Display button.
- The audit logs will be displayed in the grid. You may click on the column header to sort the data or to add more filters.
- Click on the Export button if you want to generate the report file.
- Ensure your (admin) account is member of the SYNERGIX ADCE Managed Audit Administrators security group.
- Log into a domain computer that has SYNERGIX AD Client Extensions software installed already.
- Double click on the Synergix orange icon in the system tray.
- You should see Admin Tools ( click here ) in the menu bar.
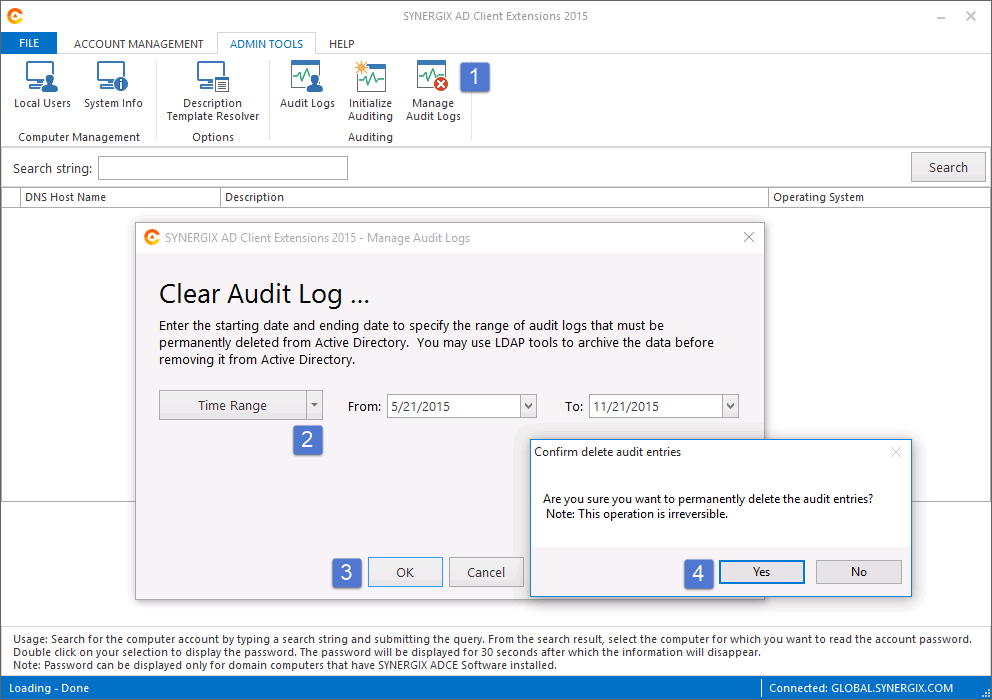
- Click on Manage Audit Logs button
- Select the time range as appropriate and click on OK.
- Click on Yes, if you are sure you want to permanently delete the Audit Log Entries.
- Once the selected Audit Entries have been removed, you can click on Cancel button to return back to the main screen in AD Client Extensions.
Test Results
- Pass or
- Fail
Test Result Submission
- Complete the Test Environment worksheet
- Upload test results document file to software test repository
- Upload log files
- ServiceLogfile.txt
- ClientLogfile.txt
- Output of GPRESULTS.EXE /V command
References
N/A


0 Comments