![]() We are no longer updating this content regularly. Please visit our knowledge base for most current version.
We are no longer updating this content regularly. Please visit our knowledge base for most current version.
Overview
This feature enables the systems administrators to manage the Built-In Administrator Account Password of the Active Directory domain computers. The Built-In Administrator Account Management feature can be configured using the Administrative Template file that is provided with the software.
The Built-In Administrator Account Password Management feature helps companies meet Data Security Standard Compliance requirements.
In a typical scenario, the IT Security Policy demands that the Built-In Administrator Account default name is renamed and its password complies with the strict password policy ( typically, complex password with 14+ characters that is changed every 60 days ) and is well secured. SYNERGIX AD Client Extensions software Built-In Administrator Account Management feature addresses this challenge by generating a complex password and changing it on a regular basis. By default the password age is set to 7 days. The local administrator account can also be renamed to a unique name on each of the domain computers running Microsoft Windows Operating System.
The software generates unique and complex password string of length 8 to 48 characters ( default is 8, recommended value is 16 ) for each computer and stores the encrypted value in Active Directory that can be retrieved by designated administrators only.
The scope of administration is managed by using an Active Directory Security group. For example a security group SYNERGIX ADCE Managed Computers may be provisioned for this purpose. The security group contains the domain computer accounts of computers installed with the software and systems administrators' domain accounts that must be allowed to retrieve password. Passwords are retrieve using the Admin Tools menu option in the SYNERGIX AD Client Extensions software.
Purpose
This article provides instructions on testing the SYNERGIX AD Client Extensions software. The Built-In Administrator Account Password Management feature is configured using the Administrative Template. After installing the Administrative Template file, the policy setting can be found under COMPUTER CONFIGURATION \ Administrative Templates \ SYNERGIX AD Client Extensions \ Local Users and Groups \ Built-In Administrator Account. The Explain tab of the Group Policy setting provides online instructions on configuring the feature.
Prerequisites
- Supported Microsoft Windows Operating System
- Microsoft Windows XP SP3 or
- Microsoft Windows Vista or
- Microsoft Windows 7.0 or
- Microsoft Windows 8.x
- Microsoft Windows 10.0
- .NET Framework
- .NET Framework 4.0 for SYNERGIX AD Client Extensions 2014 and 2015
- Domain Membership in Microsoft Active Directory domain
- Microsoft Outlook or other EMail client for Microsoft(R) Windows(TM)
- EMail client is required to submit log files to support@synergix.com or x@mail.asana.com
- SYNERGIX AD Client Extensions
Active Directory Domain Environment
- Single Active Directory Domain environment i.e. Single Forest with Forest Root Domain only example. F10.LOCAL
- You can setup a more complex Active Directory Domain environment, if needed. For example, one forest F10.LOCAL with child domains D10.F10.LOCAL, D11.F10.LOCAL and D12.F10.LOCAL and a trusted forest F20.LOCAL with child domains D20.F20.LOCAL, D21.F20.LOCAL and D22.F20.LOCAL
- Security Group(s)
- Create a security group called "SYNERGIX ADCE Managed Computers". The group type may be Domain Global Group or Domain Local Group.
- Add the test domain computer accounts into the security group "SYNERGIX ADCE Managed Computers"
- Add systems administrators domain accounts into the security group "SYNERGIX ADCE Managed Computers"
- Delegate Control
- Not applicable for configuring this feature when default attribute value otherMobile is used.
- In recommended configuration, you can select an attribute that can be marked as confidential attribute and then, delegate control to write to it. The security group "SYNERGIX ADCE Managed Computers" must be allowed to write to houseIdentifier attribute value.
- Configure domain Group Policy Object
- Copy SYNERGIX AD Client Extensions Administrative Template file SYNERGIX-ADCE.ADMX to %SystemRoot%\PolicyDefinitions on admin workstation (must be Windows 7.0 or higher)
- Copy SYNERGIX AD Client Extensions Administrative Template Language file SYNERGIX-ADCE.ADML to %SystemRoot%\PolicyDefinitions\en-US on same admin workstation (must be Windows 7.0 or higher)
- Using GPMC.MSC, edit existing or new Group Policy Object.
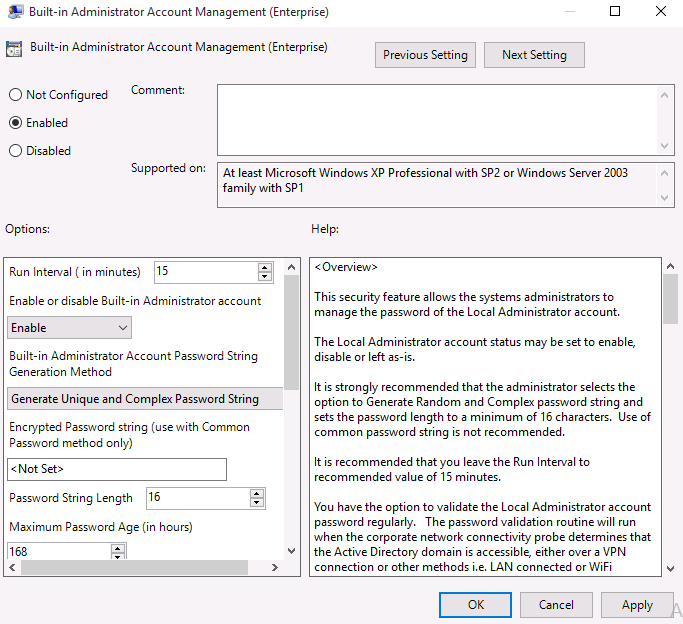
- In Group Policy Editor, expand COMPUTER CONFIGURATION
- Expand Administrative Templates
- Expand SYNERGIX AD Client Extensions
- Expand Local Users and Groups
- Select Built-In Administrator Account Password
- Click on the Enable radio button to enable the policy setting
- For administrator account status, select Enable, Disable or Leave as-is. Default is to have it Enabled
- For Password String Generation Method, select Generate Unique and Complex Password. This option is strongly recommended.
- If you wish to assign same password to the Built-In Administrator Account on all client computers with SYNERGIX ADCE installed, type the encrypted password string. You will need external tool from the vendor to generate the encrypted password for your Active Directory domain environment.
- Set Password Policy, as appropriate. Default values i.e. Password length ( 8 characters ) , Minimum Password Age ( 7 days ) and Password Validation Interval ( 1,440 minutes ) are recommended. It is strongly recommended that you set the Password Length to a minimum of 16 characters.
- By default, the encrypted password is stored in the chosen multi-valued attribute of the computer object and replicated to all domain controllers as part of normal Active Directory replication cycle.
- In basic configuration, it is recommended the default setting for the multi-valued attribute is not changed.
- In advanced configuration, you may select attribute value like houseIdentifier and mark it as confidential in the schema. You will be required to also delegate control by granting WRITE properties on the houseIdentifier attribute value.
- Click OK to save the Group Policy settings.
More Information
- Visit Synergix website or contact vendor support
Procedure
- Ensure your (admin) account is member of the SYNERGIX ADCE Managed Computers security group
- Log into a domain computer with the domain account ( your admin account ) that has local administrative privileges on the workstation.
- Ensure the SYNERGIX AD Client Extensions specific Group Policy settings were applied
- Launch RSOP.MSC or run GPRESULT.EXE /v to confirm
- Install SYNERGIX AD Client Extensions software
- After the software is successfully installed, double click on the orange icon in the system tray.
- You should see Admin Tools in the menu bar. It is visible only to members of the SYNERGIX ADCE Managed Computers security group.
- In the Search String enter the first three characters of domain computers which you want to retrieve the password.
- Select a computer from the list. Double click on it. You should be able to see the decrypted password string for the Built-In Administrator Account..
- You can use the Backup Administrator Account Password GPO setting to create a new local account ( Backup Administrator ) and manage Backup Administrator Account Password. By default, the backup administrator account is created using the su-%computername% template
- Note the acronym su simply means super user. You can create a template of your choice.
Test Results
- Pass or
- Fail
Tip: You can run the following command to validate the Password Last Set Date / Time
NET USER ADMINISTRATOR
User name Administrator
Full Name
Comment Built-in account for administering the computer/domain
User's comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 6/25/2015 9:37:26 PM
Password expires Never
Password changeable 6/25/2014 9:37:26 PM
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 6/25/2015 9:38:48 PM
Logon hours allowed All
Local Group Memberships *Administrators
Global Group memberships *None
The command completed successfully.
Test Result Submission
- Complete the Test Environment worksheet
- Upload test results document file to software test repository
- Upload log files
- ServiceLogfile.txt
- ClientLogfile.txt
- Output of GPRESULTS.EXE /V command
References
N/A


0 Comments